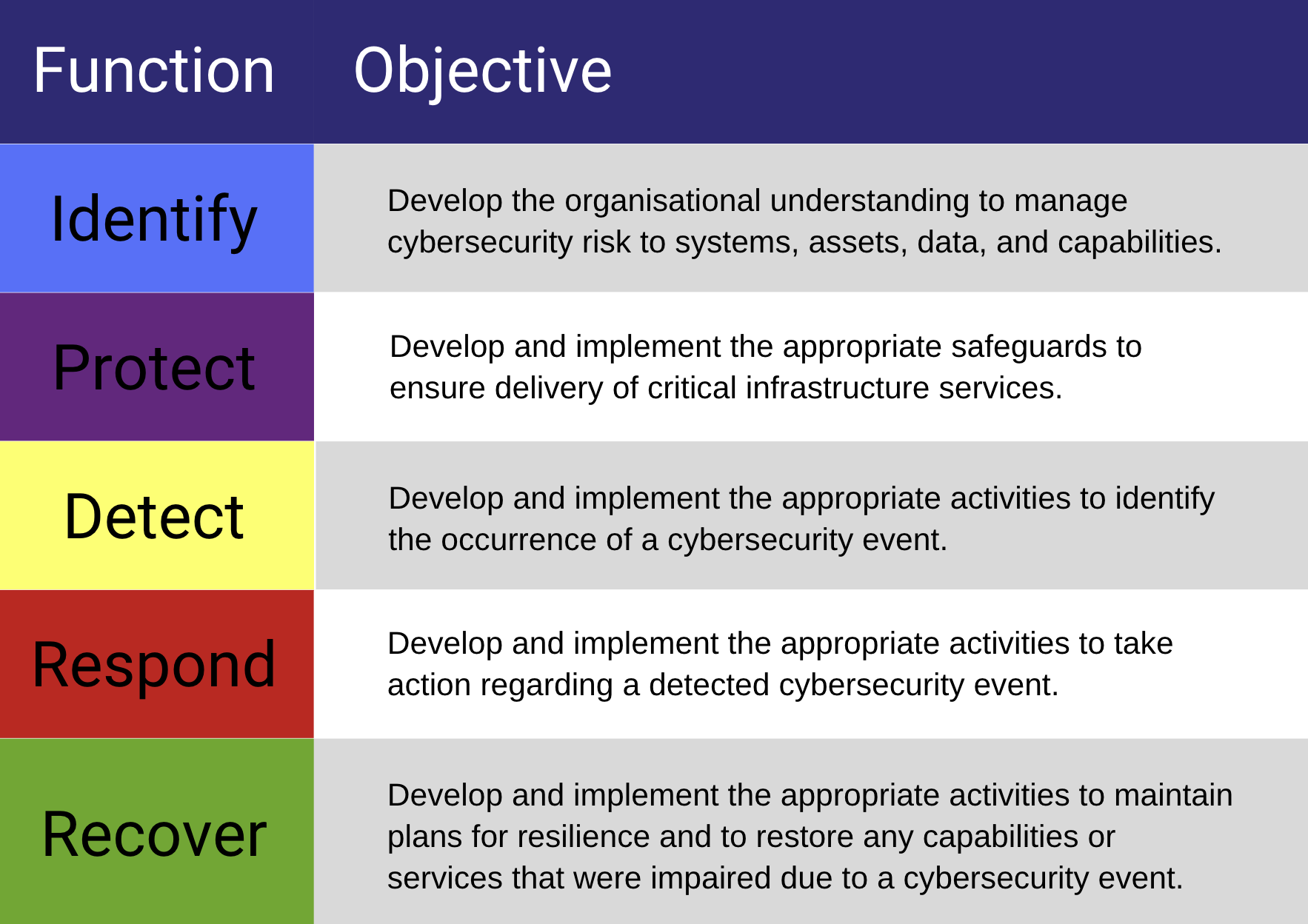
The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories . implementation guidance in addition to the controls and control enhancements. the core consists of three parts: organizations planning to implement an access control system should consider three abstractions: This pdf is produced from oscal source data and represents a derivative format of. this learning module takes a deeper look at the cybersecurity framework's five functions: The access control policy is implemented under the protect function of the nist cybersecurity. an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. The core includes five high level functions: one new control and three supporting control enhancements related to identity providers, authorization servers,.
from mavink.com
The core includes five high level functions: the core consists of three parts: organizations planning to implement an access control system should consider three abstractions: This pdf is produced from oscal source data and represents a derivative format of. implementation guidance in addition to the controls and control enhancements. The access control policy is implemented under the protect function of the nist cybersecurity. an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. one new control and three supporting control enhancements related to identity providers, authorization servers,. this learning module takes a deeper look at the cybersecurity framework's five functions:
Nist Framework Explained
The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. The access control policy is implemented under the protect function of the nist cybersecurity. organizations planning to implement an access control system should consider three abstractions: The core includes five high level functions: implementation guidance in addition to the controls and control enhancements. this learning module takes a deeper look at the cybersecurity framework's five functions: This pdf is produced from oscal source data and represents a derivative format of. the core consists of three parts: an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. one new control and three supporting control enhancements related to identity providers, authorization servers,.
From www.comparitech.com
NIST Cybersecurity Framework Guide 2024 Core, Implementation & Profile The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories The access control policy is implemented under the protect function of the nist cybersecurity. one new control and three supporting control enhancements related to identity providers, authorization servers,. This pdf is produced from oscal source data and represents a derivative format of. an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. The core includes. The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories.
From www.slideteam.net
Nist Framework Implementation Tier Categories PPT Template The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories implementation guidance in addition to the controls and control enhancements. This pdf is produced from oscal source data and represents a derivative format of. this learning module takes a deeper look at the cybersecurity framework's five functions: organizations planning to implement an access control system should consider three abstractions: The core includes five high level functions: The. The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories.
From www.nist.gov
An Introduction to the Components of the Framework NIST The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories organizations planning to implement an access control system should consider three abstractions: this learning module takes a deeper look at the cybersecurity framework's five functions: an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. This pdf is produced from oscal source data and represents a derivative format of. The access control policy is. The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories.
From www.researchgate.net
Functions, Categories, and Subcategories of NISTCSF Framework [37]. Download Scientific Diagram The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories implementation guidance in addition to the controls and control enhancements. This pdf is produced from oscal source data and represents a derivative format of. the core consists of three parts: this learning module takes a deeper look at the cybersecurity framework's five functions: organizations planning to implement an access control system should consider three abstractions: . The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories.
From www.techtarget.com
What is NIST? Everything You Should Know About NIST Compliance The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories this learning module takes a deeper look at the cybersecurity framework's five functions: the core consists of three parts: an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. This pdf is produced from oscal source data and represents a derivative format of. The core includes five high level functions: one new control. The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories.
From www.csi-tools.com
The NIST framework for SAP Access Security, with CSI tools' help. The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. this learning module takes a deeper look at the cybersecurity framework's five functions: The access control policy is implemented under the protect function of the nist cybersecurity. one new control and three supporting control enhancements related to identity providers, authorization servers,. the core. The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories.
From www.securityscientist.net
20 NIST Control Families The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories The access control policy is implemented under the protect function of the nist cybersecurity. one new control and three supporting control enhancements related to identity providers, authorization servers,. This pdf is produced from oscal source data and represents a derivative format of. this learning module takes a deeper look at the cybersecurity framework's five functions: The core includes. The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories.
From opscompass.com
Introduction to the NIST Cybersecurity Framework The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories organizations planning to implement an access control system should consider three abstractions: The core includes five high level functions: an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. implementation guidance in addition to the controls and control enhancements. The access control policy is implemented under the protect function of the nist cybersecurity. . The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories.
From kanini.com
5 functions of NIST Cybersecurity (CSF) Framework KANINI The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories The core includes five high level functions: an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. implementation guidance in addition to the controls and control enhancements. The access control policy is implemented under the protect function of the nist cybersecurity. one new control and three supporting control enhancements related to identity providers, authorization. The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories.
From data1.skinnyms.com
Nist 800171 Access Control Policy Template The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories The core includes five high level functions: this learning module takes a deeper look at the cybersecurity framework's five functions: The access control policy is implemented under the protect function of the nist cybersecurity. an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. organizations planning to implement an access control system should consider. The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories.
From de.tenable.com
NIST 80053 Authentication and Access Control SC Dashboard Tenable® The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories implementation guidance in addition to the controls and control enhancements. this learning module takes a deeper look at the cybersecurity framework's five functions: an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. organizations planning to implement an access control system should consider three abstractions: The access control policy is implemented under the. The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories.
From www.securityscientist.net
20 NIST Control Families The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories the core consists of three parts: organizations planning to implement an access control system should consider three abstractions: one new control and three supporting control enhancements related to identity providers, authorization servers,. The access control policy is implemented under the protect function of the nist cybersecurity. implementation guidance in addition to the controls and control enhancements.. The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories.
From www.researchgate.net
Function and Category NIST CSF [6] Download Scientific Diagram The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories organizations planning to implement an access control system should consider three abstractions: The access control policy is implemented under the protect function of the nist cybersecurity. This pdf is produced from oscal source data and represents a derivative format of. this learning module takes a deeper look at the cybersecurity framework's five functions: one new control and. The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories.
From www.hyperglance.com
Implement The NIST Cybersecurity Framework using Hyperglance The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories implementation guidance in addition to the controls and control enhancements. one new control and three supporting control enhancements related to identity providers, authorization servers,. This pdf is produced from oscal source data and represents a derivative format of. this learning module takes a deeper look at the cybersecurity framework's five functions: The access control policy is implemented. The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories.
From sprinto.com
An Ultimate Guide to NIST Access Controls Requirements Sprinto The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories one new control and three supporting control enhancements related to identity providers, authorization servers,. an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. the core consists of three parts: The core includes five high level functions: The access control policy is implemented under the protect function of the nist cybersecurity. organizations planning. The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories.
From www.goodreads.com
Verification and Test Methods for Access Control Policies/Models NIST SP 800192 by National The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories the core consists of three parts: implementation guidance in addition to the controls and control enhancements. organizations planning to implement an access control system should consider three abstractions: This pdf is produced from oscal source data and represents a derivative format of. one new control and three supporting control enhancements related to identity providers, authorization servers,.. The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories.
From www.enzoic.com
Surprising Password Guidelines from NIST Enzoic The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories organizations planning to implement an access control system should consider three abstractions: The access control policy is implemented under the protect function of the nist cybersecurity. the core consists of three parts: an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. this learning module takes a deeper look at the cybersecurity framework's. The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories.
From templates.esad.edu.br
Nist 800171 Access Control Policy Template The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories the core consists of three parts: one new control and three supporting control enhancements related to identity providers, authorization servers,. this learning module takes a deeper look at the cybersecurity framework's five functions: This pdf is produced from oscal source data and represents a derivative format of. The core includes five high level functions: an access. The Access Control Policy Is Implemented For Which Nist Function And Sub-Categories.